Robot Management Layer (RML)
Overview
RML is the on-robot service that manages all external communication between the robot and cloud/edge infrastructure. It runs as a daemon with a small set of libraries and exposes two stable entry points to applications and operators:
- gRPC control/state API - authenticated, bidirectional commands and structured status
- WebRTC media - real-time video/audio and data channels via an SFU
Architecture
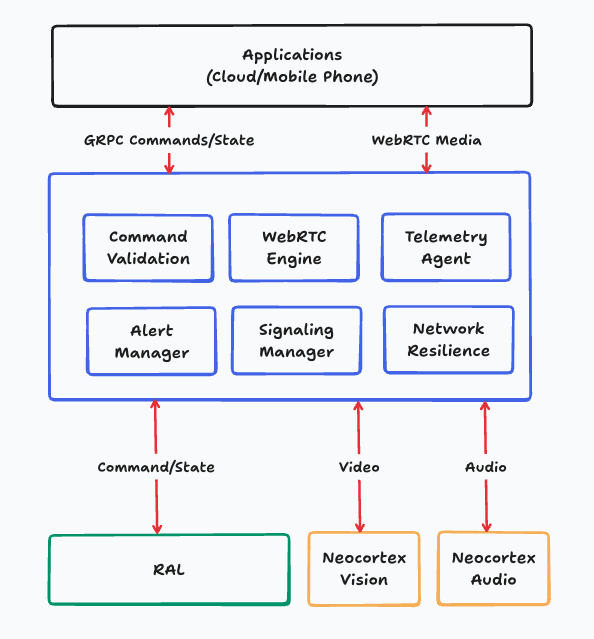
The Four Pipelines
RML runs four independent, cooperating pipelines on top of shared security, networking, and scheduling.
Media Pipeline (robot → cloud)
Handles real-time video/audio from robot to cloud.
Data Flow:
What’s optimized:
- Zero-copy ingest: RML reads encoded frames/packets by pointer from shared memory rings (no memcpy).
- WebRTC adaptation: TWCC/TCC, RTCP feedback, bandwidth estimators; simulcast enables per-viewer quality.
- Priority: Audio and control data outrank video when bandwidth is tight.
Telemetry Pipeline (robot ↔ cloud)
Pushes metrics for complete observability.
Data Flow:
Why 100 Hz vs 1 Hz?
- Robot state (joints, IMU, battery) changes at control rates; we sample at 100 Hz and downsample intelligently (e.g., unchanged joint positions suppressed).
- System metrics (CPU, thermal, memory) evolve slowly; 1 Hz captures meaningful trends without noise or overhead.
Command Pipeline (cloud → robot)
Carries teleoperation commands down to hardware with rigorous validation.
Data Flow:
On failure
- NACK with structured error codes (UNAUTHORIZED, STALE, RATE_LIMITED, SAFETY_VIOLATION, CONFLICT).
- Not applied to hardware; kept in audit log with reason.
- Optional alert if violations repeat (rate-limited to avoid noise).
Emergency Stop
- Minimal authentication (must be legitimate source).
- Skips dedup/time/rate checks for speed.
- Does not bypass hardware safety; mechanical/electrical limits still enforced.
- Direct path to RAL “hard-stop” → stop/hold/brake within milliseconds.
2.4 Alert Pipeline
Data Flow:
Routing policy (examples)
- Critical hardware (over-temp, driver fault, e-stop): page on-call immediately.
- Network issues: notify ops channel; auto-create incident if sustained.
- Informational: daily/weekly summaries.
- Escalation: if unacknowledged within SLO, escalate per schedule.
Cross-Cutting Features
Network Resilience
Adaptive Strategies:
Network Quality RML Response
─────────────── ────────────
Excellent (>10Mbps) ──▶ 4K video, 60fps, full telemetry
Good (2-10Mbps) ──────▶ 1080p, 30fps, sampled telemetry
Fair (500kb-2Mbps) ───▶ 480p, 15fps, critical telemetry
Poor (<500kbps) ──────▶ Audio only, commands, alerts onlyData Prioritization (when bandwidth limited):
- Teleoperation commands (never dropped)
- Emergency alerts
- Basic telemetry
- Audio stream
- Video stream (degraded/paused)
- Detailed telemetry (buffered)
Security Architecture
Defense in Depth:
- Authentication: TLS, API keys with rotation
- Authorization: RBAC with per-command permissions
- Encryption: TLS (control), DTLS-SRTP (media)
- Audit: Every command logged with UUID, timestamp, signature
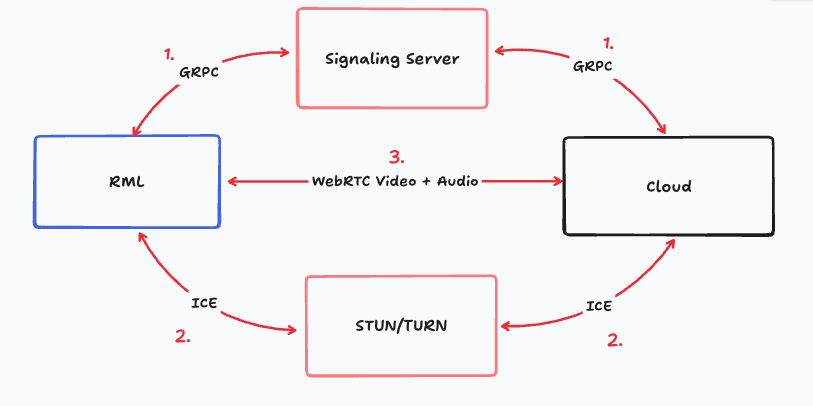
WebRTC Integration
Last updated on